ghctf

ghctf
grandre
ASM?Signin!
ai 一把梭
1 | #!/usr/bin/env python3 |
FishingKit
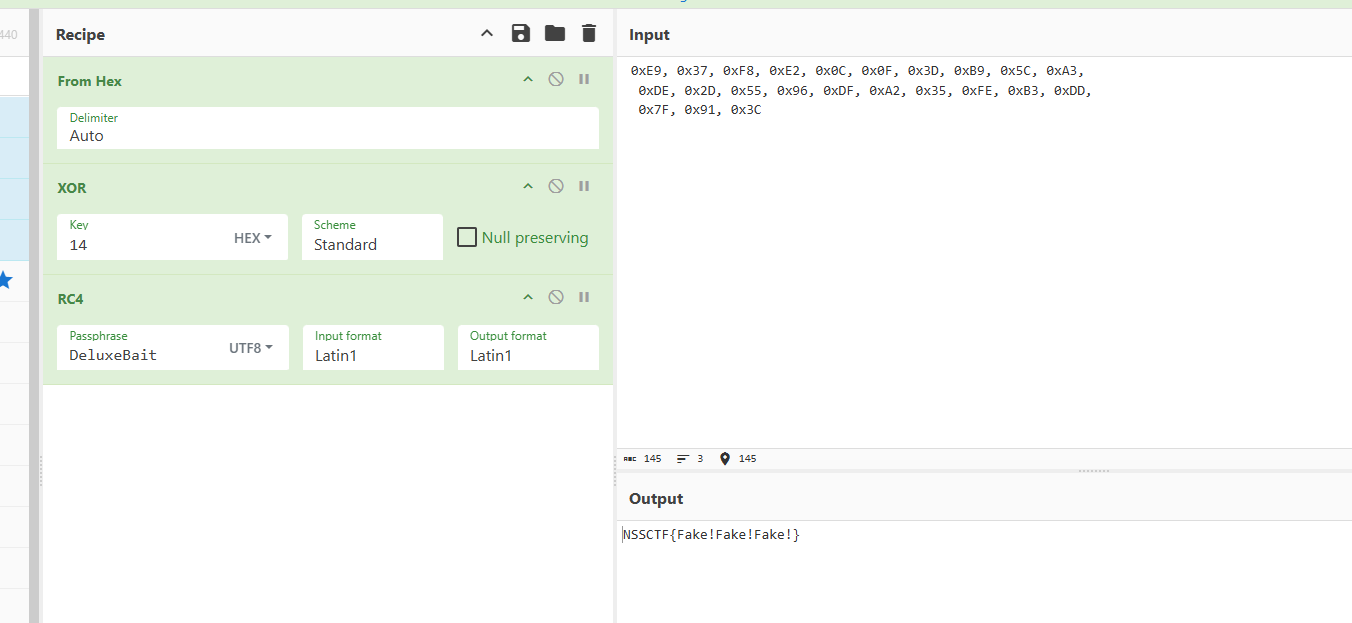
main函数解出是假的flag
1 | from z3 import * |
继续看
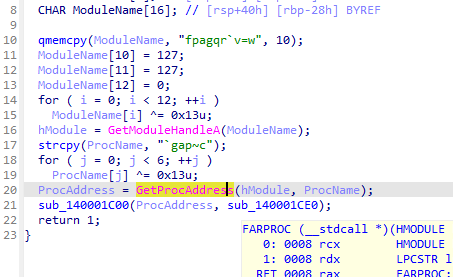
GetModuleHandleA 函数 (libloaderapi.h) - Win32 apps | Microsoft Learn
GetProcAddress 函数 (libloaderapi.h) - Win32 apps | Microsoft Learn
VirtualProtect 函数 (memoryapi.h) - Win32 应用程序 |Microsoft 学习
查看
三个方法 挨个看
继续进入查看
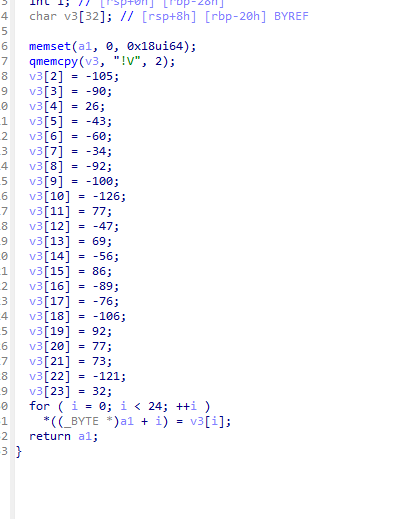
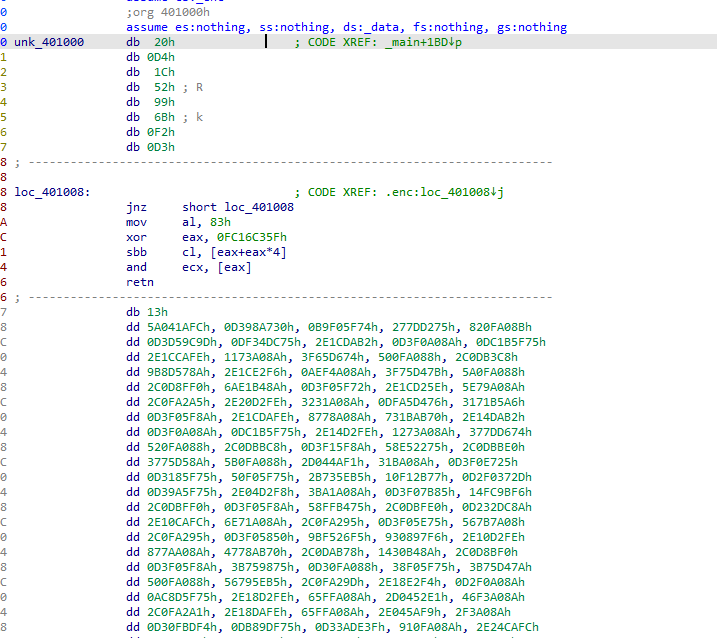
密文没加载
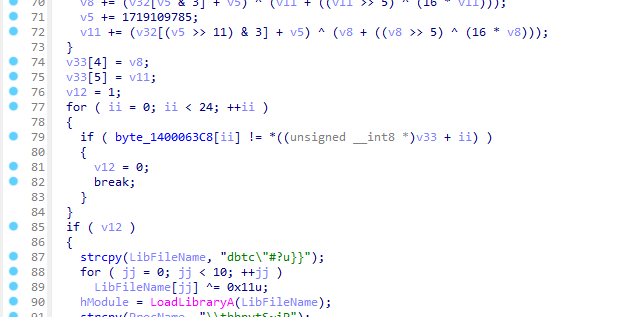
另一个方法就是初始化密文 key就是z3解的 我没仔细调试 猜的 端序 脚本一把嗦
1 | #include <iostream> |
LockedSecret
upx改了标志位
不难但是折磨
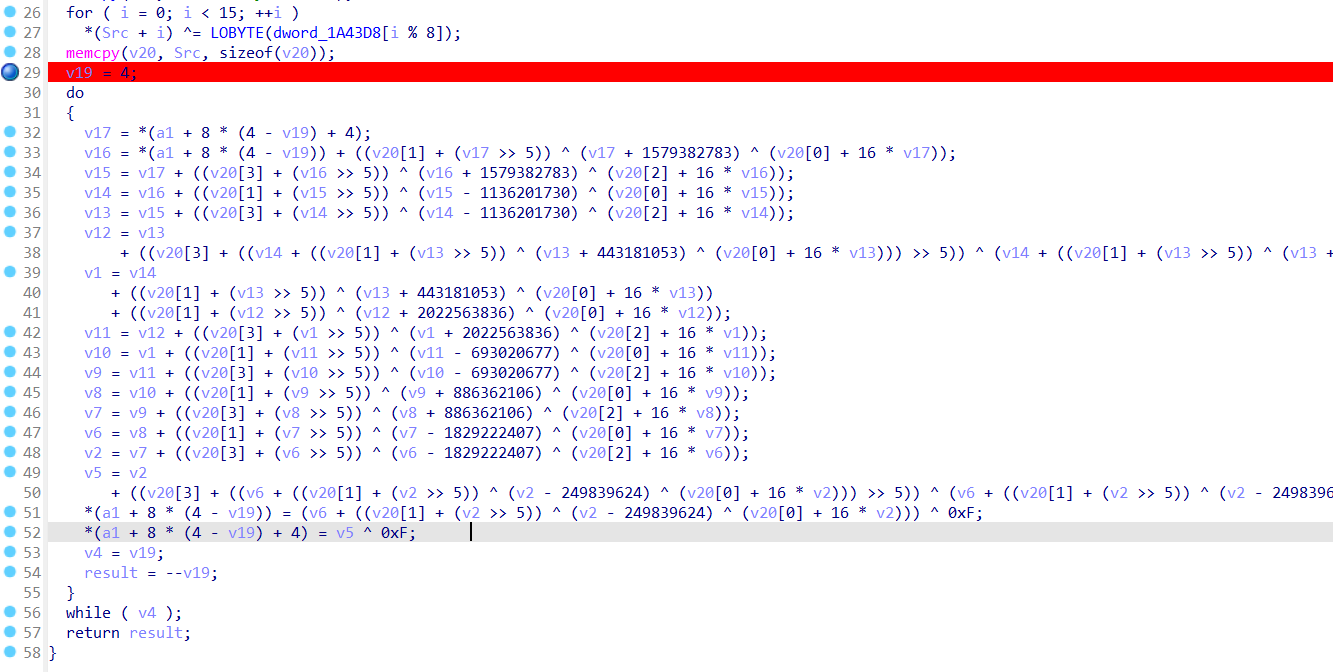
我勒个超级大tea啊 直接逆
NSSCTF{!!!Y0u_g3t_th3_s3cr3t!!!}
TimeSpaceRescue
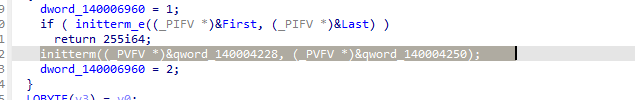
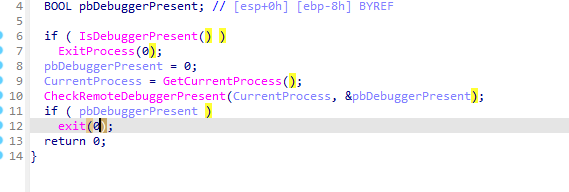
开始逆天了 开局闪退 找退出位置
初始化就退
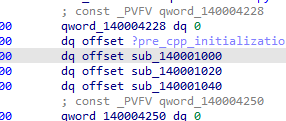
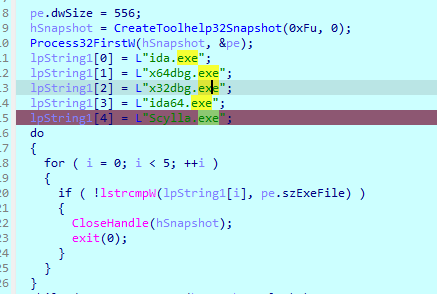
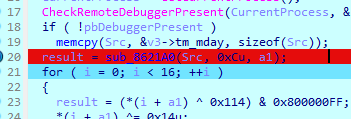
一堆的反调试
检测应用名 最外层的函数直接删除就完了
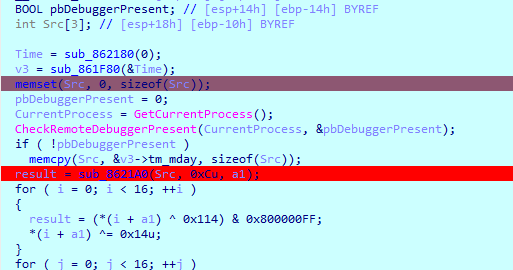
获取时间戳 获取md5 这里会有花指令 处理一下就行
原来是去pe文件结构里面找时间戳 但是根据题目来看并不是 爆破 嘤嘤嘤
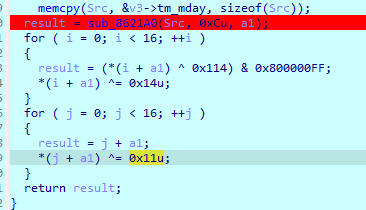
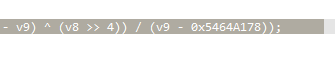
md5赋值给a1 下面进行异或 看aes的部分 魔改挺多 心态大爆炸
这题主要的问题就是把时间戳搞出来 爆破了
1 |
|
Room 0
难绷
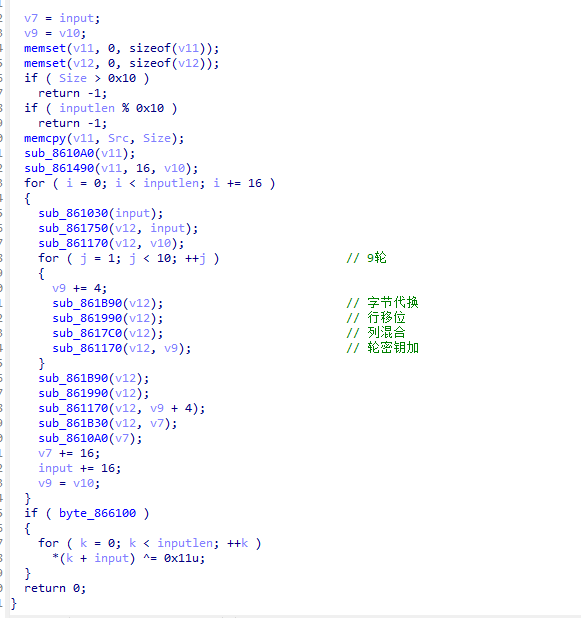
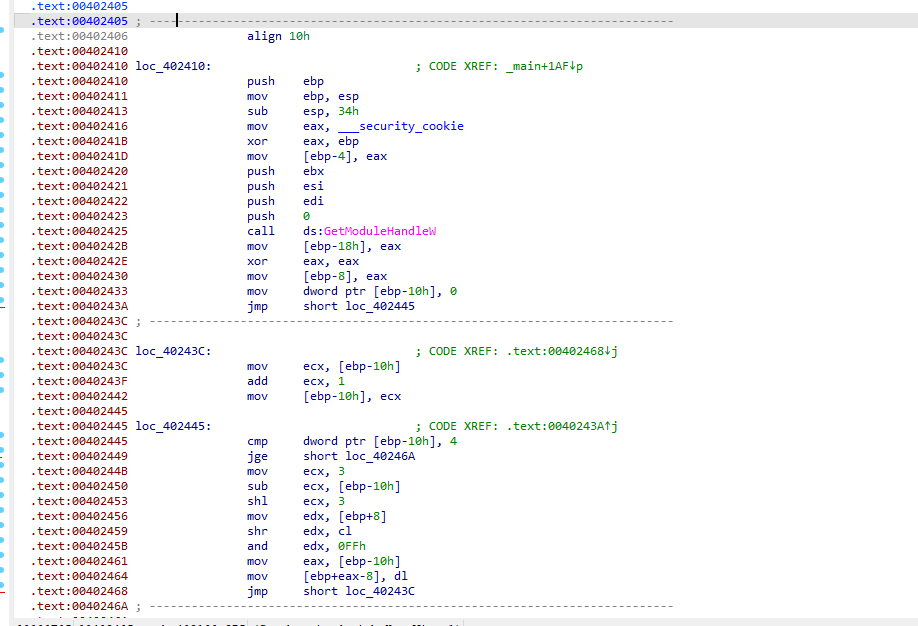
花指令
处理一下 这题有点像那个hgame的异常处理 忘了 也是一堆的花指令要修
异常处理
修复完花指令就是指令
这里是那个key转换 4字节 ctrl s直接到对应的段
说一下 怎么找 首先初始化栈帧的前三位是固定的 第四位就是异常的触发点
这里 让后面为0就行
1 | #include<stdio.h> |
得到755ff0d3就是key
再去解smc
1 | print("A" * 32) |
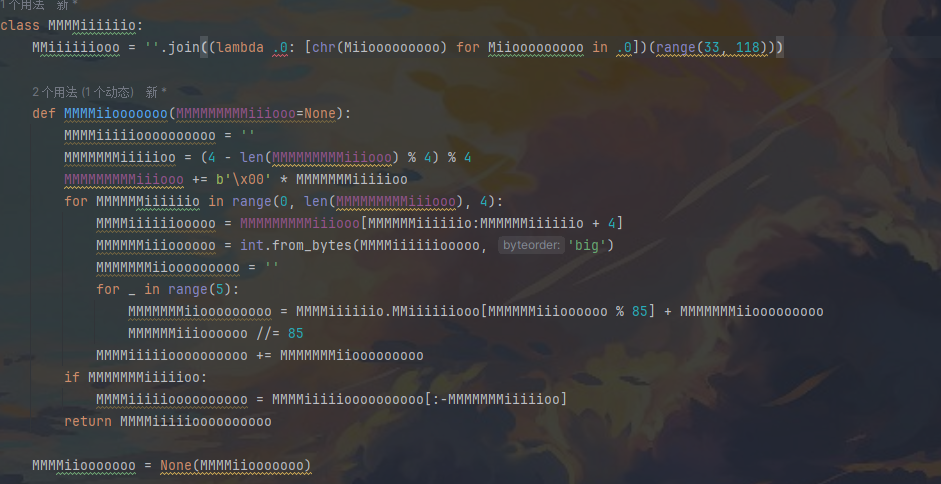
Mio?Ryo?Soyo?
当时就不应该偷懒没安pyenv 这题要用python3.8 不然解包的时候库的pyc导不出来
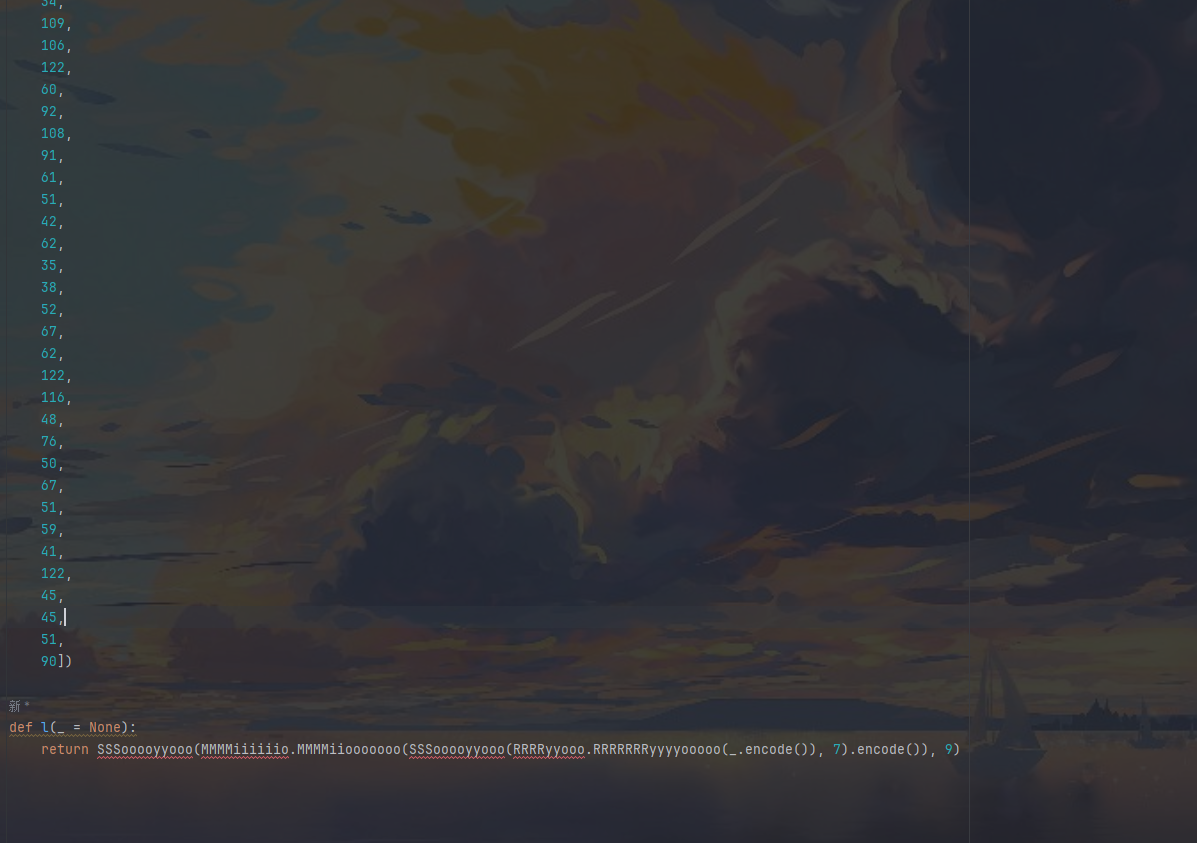
密文和l函数的加密流程
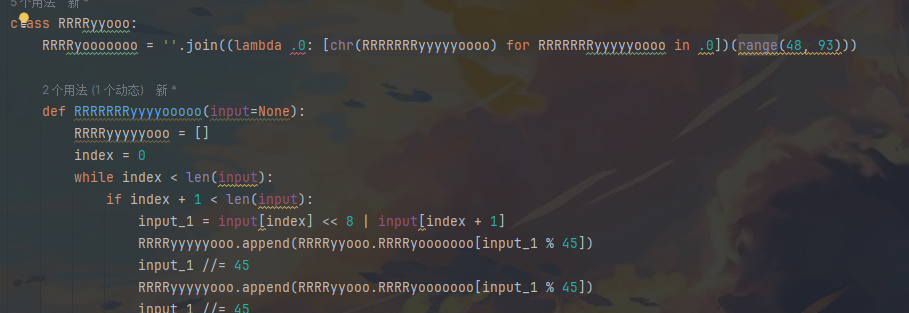
从range那里大概就可以知道是一个base45的加密
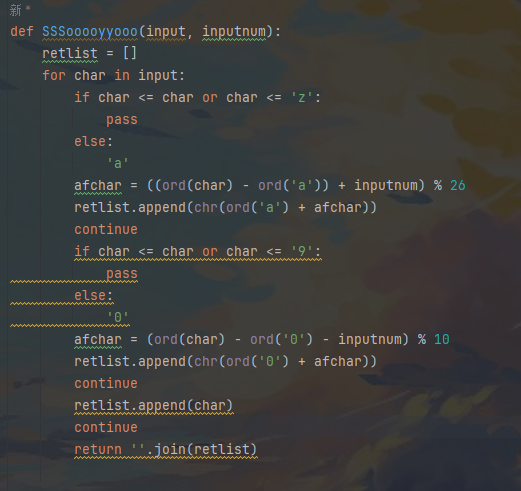
稍微修一下 就是简单的判断 修改字符
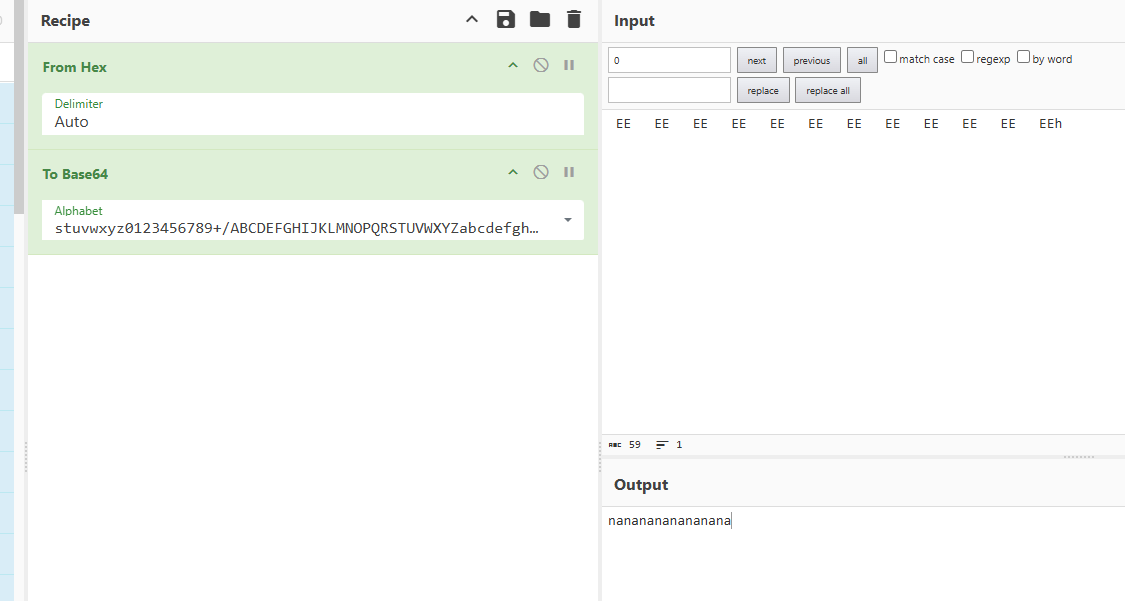
base85 已经红了 流程就是base45 修改字符 base85 修改字符 倒序即可
1 | sssssssssssss = bytes( |
canon
两层的vm 内层感觉还好 跟进一下流程 没上太大强度
1 | #include<stdio.h> |
1 | fun3 input1, input2, 1 修改input1 input2没变 |
跟进一下base 不是标准的说实话真不想写了 输入
1 | aaaaaaaaaaaabbbbbbbbbbbbcccccccccccc |
标准的 能玩 再去细看 op对应的操作都是什么 把对应的解密函数写出来 纯纯代码量 都是可逆的 这里我是手解的 直接copy官方wp了
1 | import base64 |
腐蚀
rust题 最难绷的一集
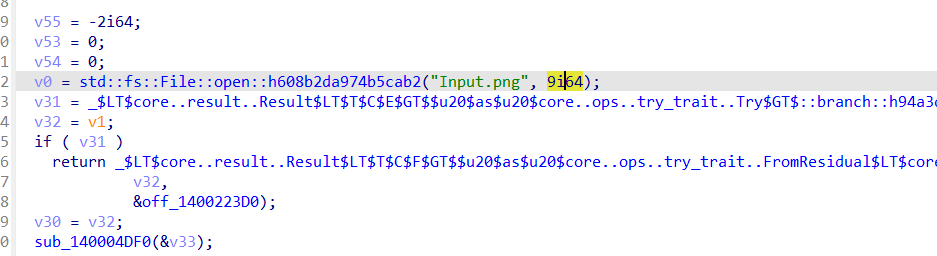
读取文件
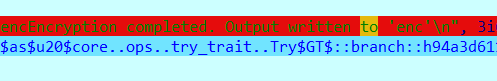
将内容返回给enc文件
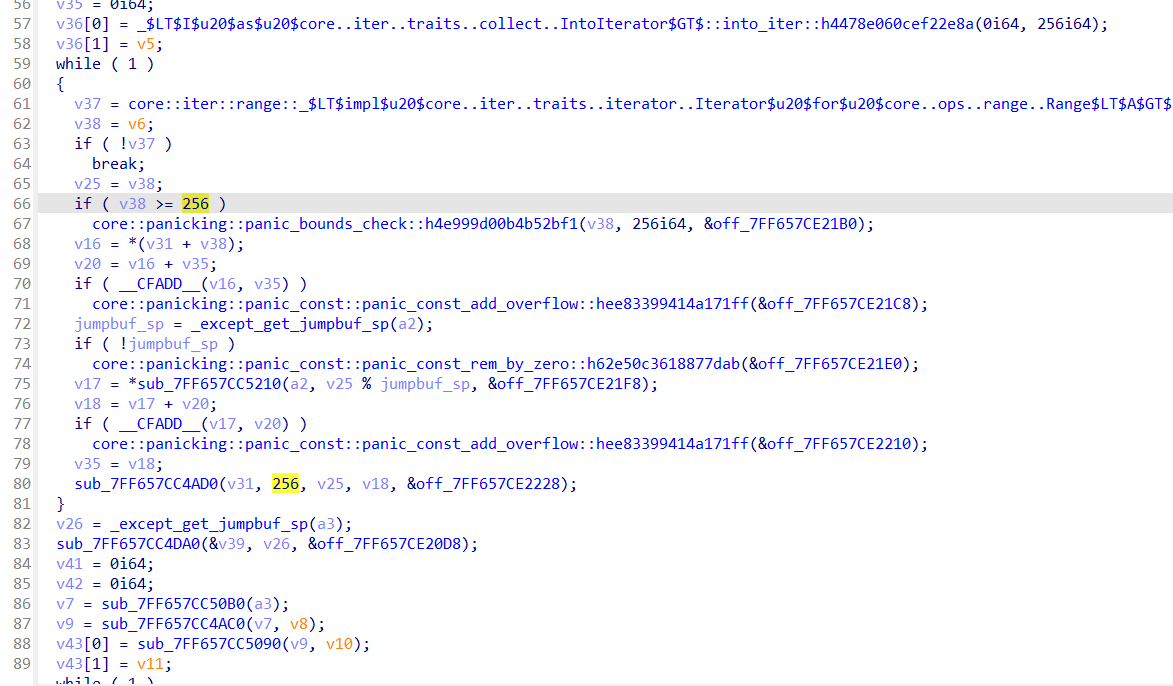
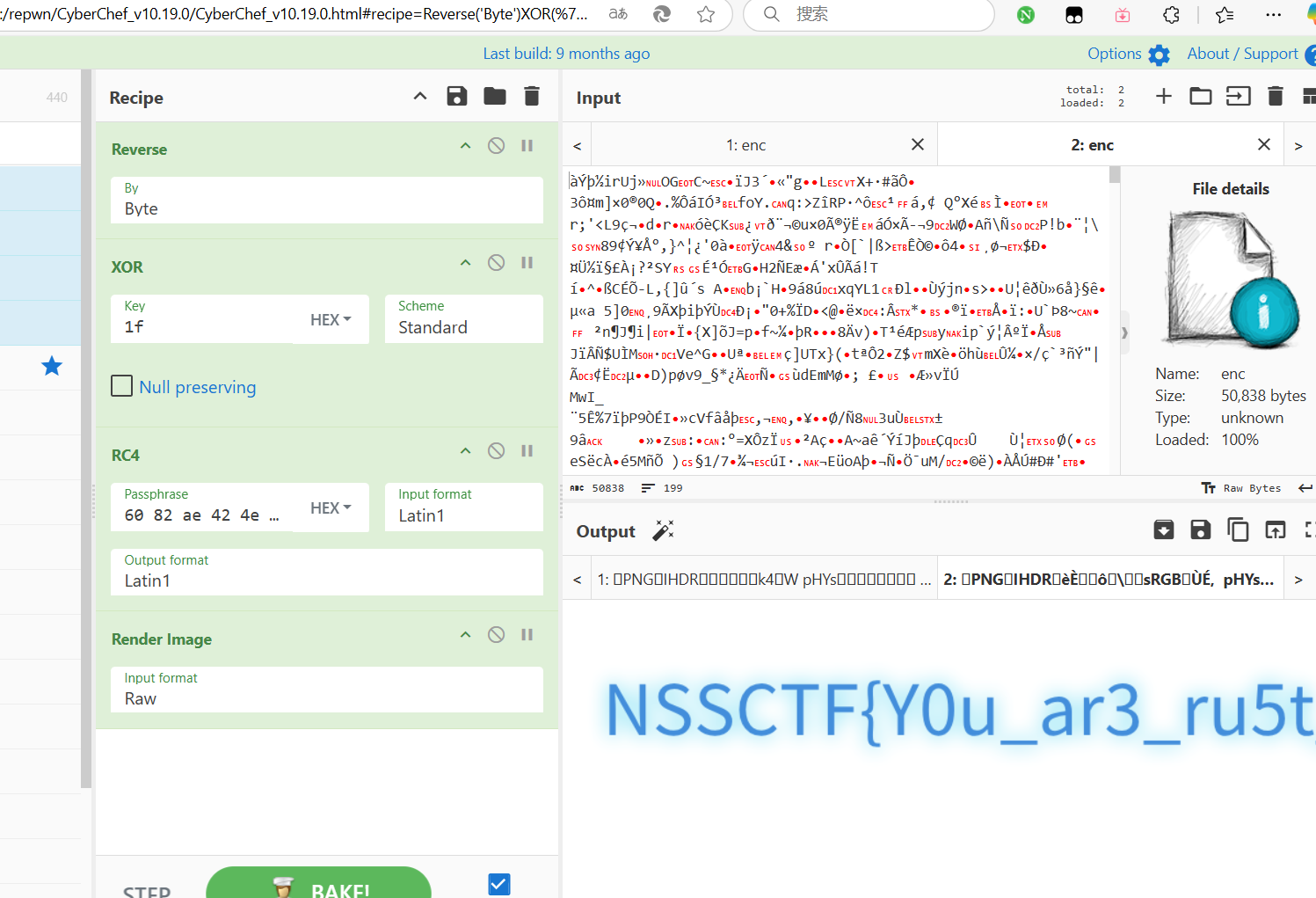
进入这个函数 256 rc4
明显就是sbox
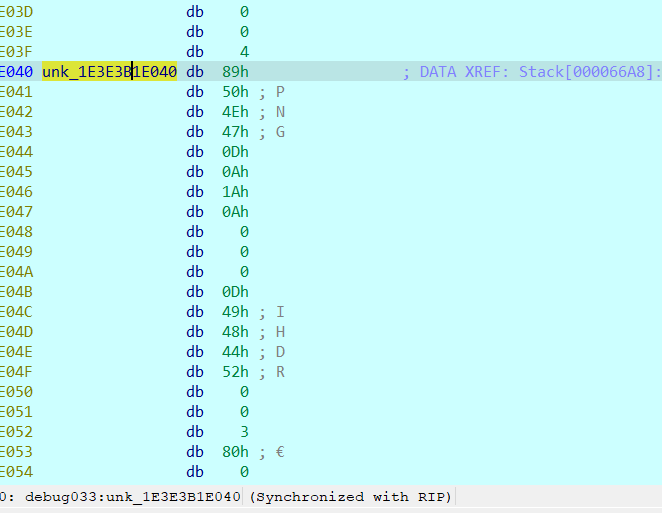
这是我们自定义png里面的东西
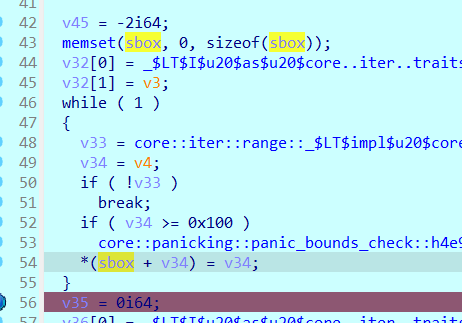
这里就是我们初始化sbox的地方
可以手动调试可以看见sbox的东西已经进行了修改
这里就是key的东西 打乱了一下顺序但是问题不大 key为我们输入的前8位和后八位 并且打乱顺序 png文件的头尾还是好确定的
我直接上网找了一个png (懒得找png头尾都是啥)
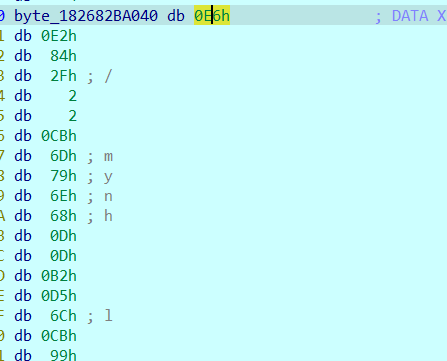
1 | 0x60, 0x82, 0xAE, 0x42, 0x4E, 0x44, 0x49, 0x45, 0x1A, 0x0A, 0x0D, 0x0A, 0x4E, 0x47, 0x89, 0x50 |
继续 在下面的a1可以找到我们的内容
这里看得见 我们加密以后的数据
仔细去对比数据会发现这东西他是会翻转的
(最后的翻转确实是没想到 差点炸缸)
ezObfus
花指令量大管饱 两眼一黑 好在没上什么逆天的花 不好认
还有一些零散的就不一一展示了(写不动了)
对key进行处理 查一下上面的特征可以知道是个hash 下面有个校验的函数 爆破
1 | 8C90F77B |
直接四层大循环套着跑就完了 以十进制输入
1 | import ctypes |
crypto
baby_factor
1 | from Crypto.Util.number import long_to_bytes |
baby_signin
1 | from Crypto.Util.number import long_to_bytes |
EZ_Fermat
1 | #!/usr/bin/env python3 |
pwn
爆0
web
misc
爆0