litctf-re

litctf-re
grandlit的时候忙其他的去了只能含泪复现 rc4的附件不知道丢哪了 整体的难度还行
FeatureExtraction
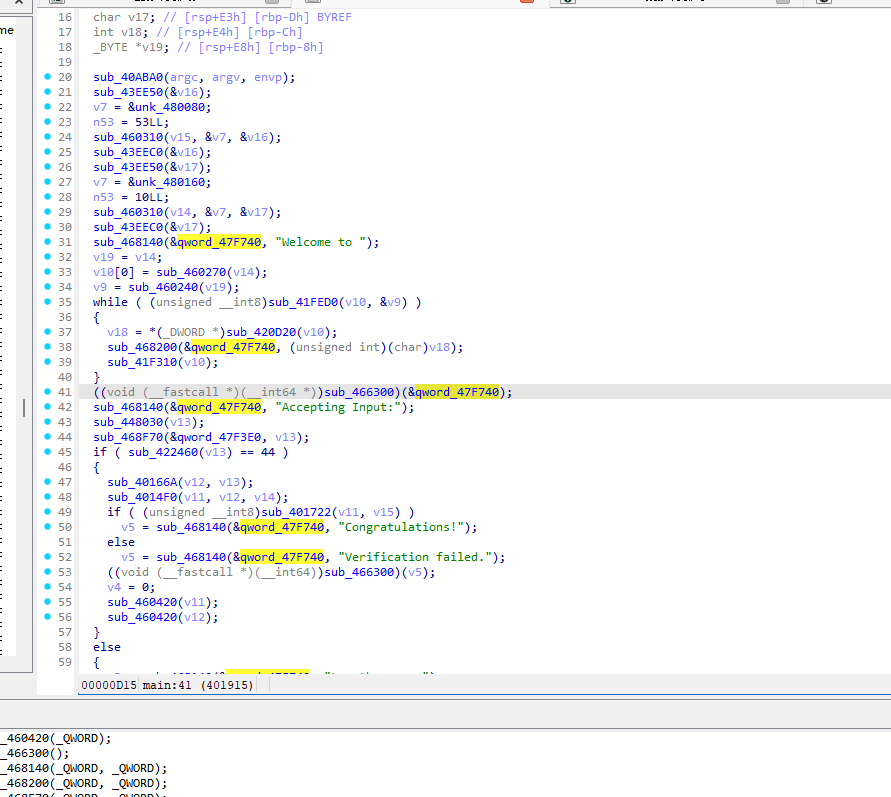
将我们的输入处理为32位
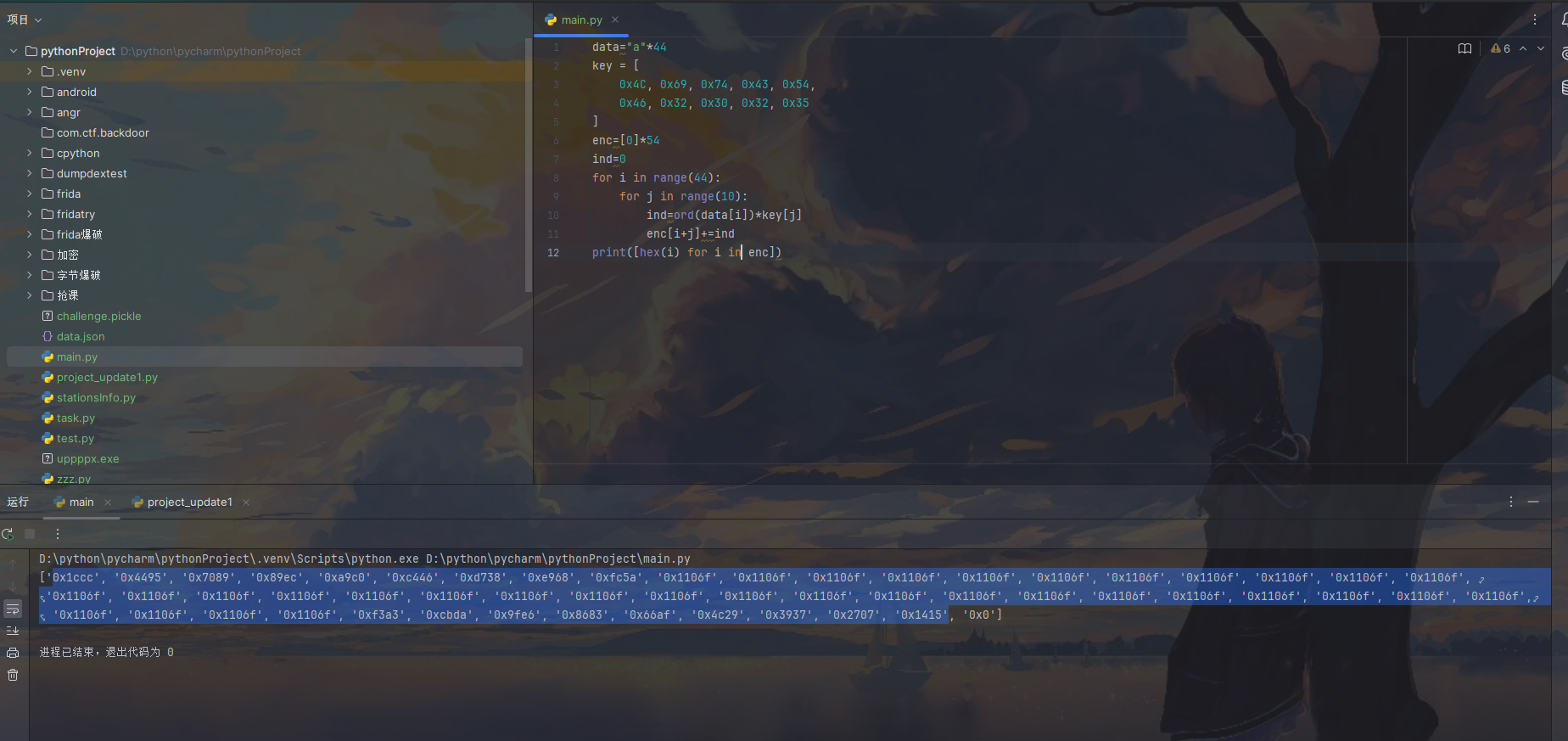
发现到key
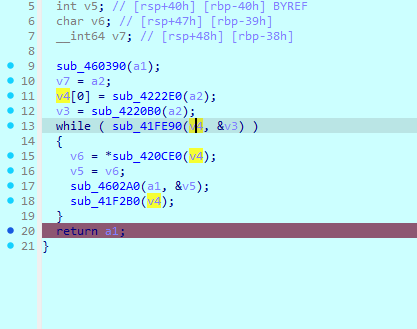
进入加密函数观察加密流程
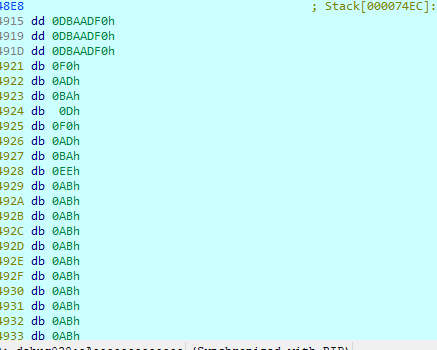
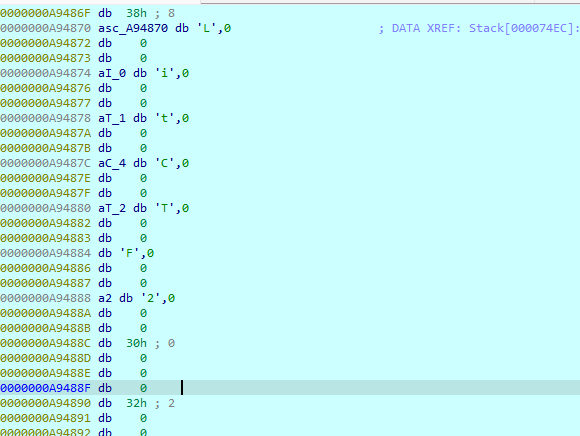
搞到密文
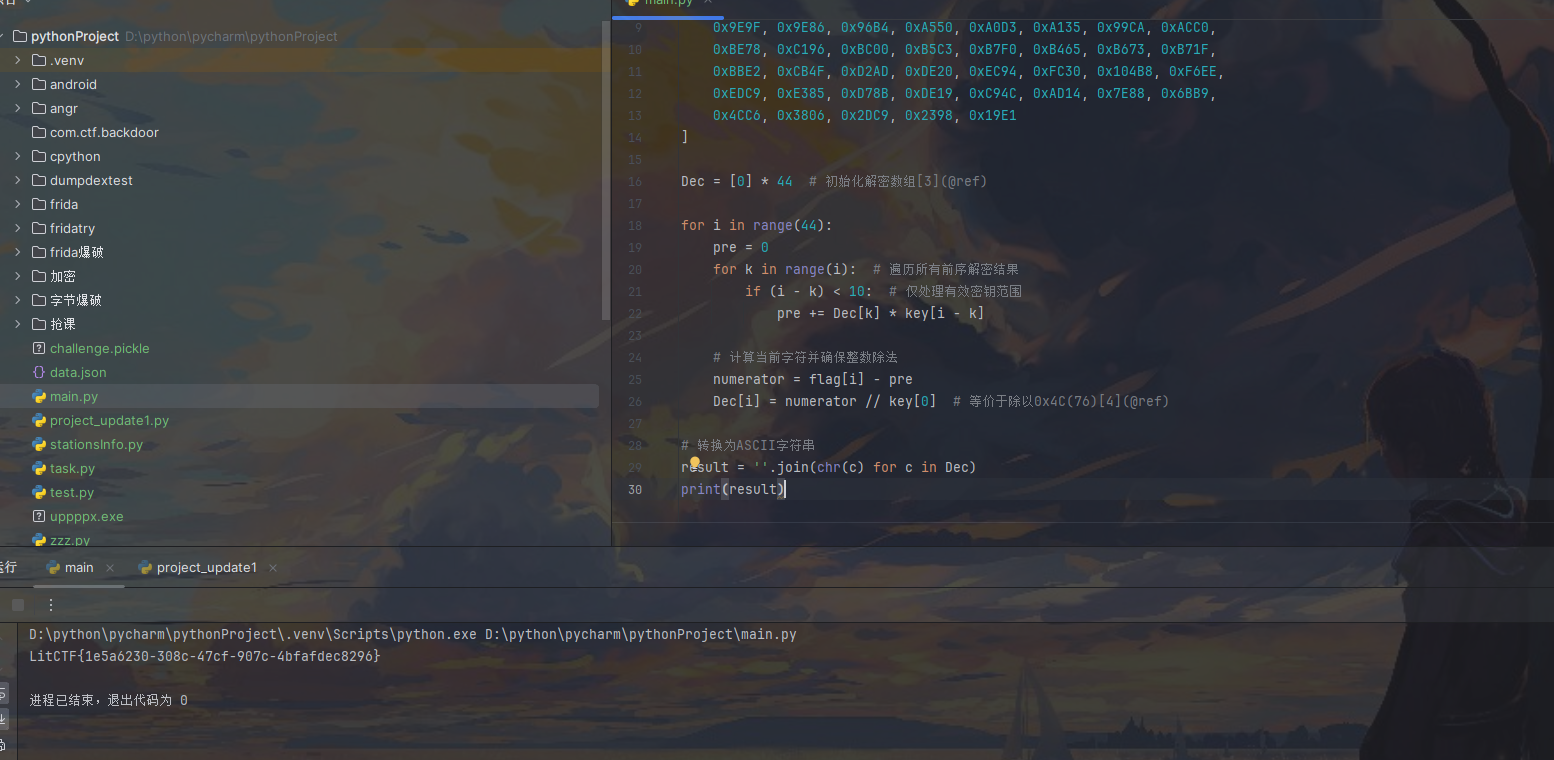
理解加密流程 解密就简单了
1 | key = [0x4C, 0x69, 0x74, 0x43, 0x54, 0x46, 0x32, 0x30, 0x32, 0x35] |
easy_tea
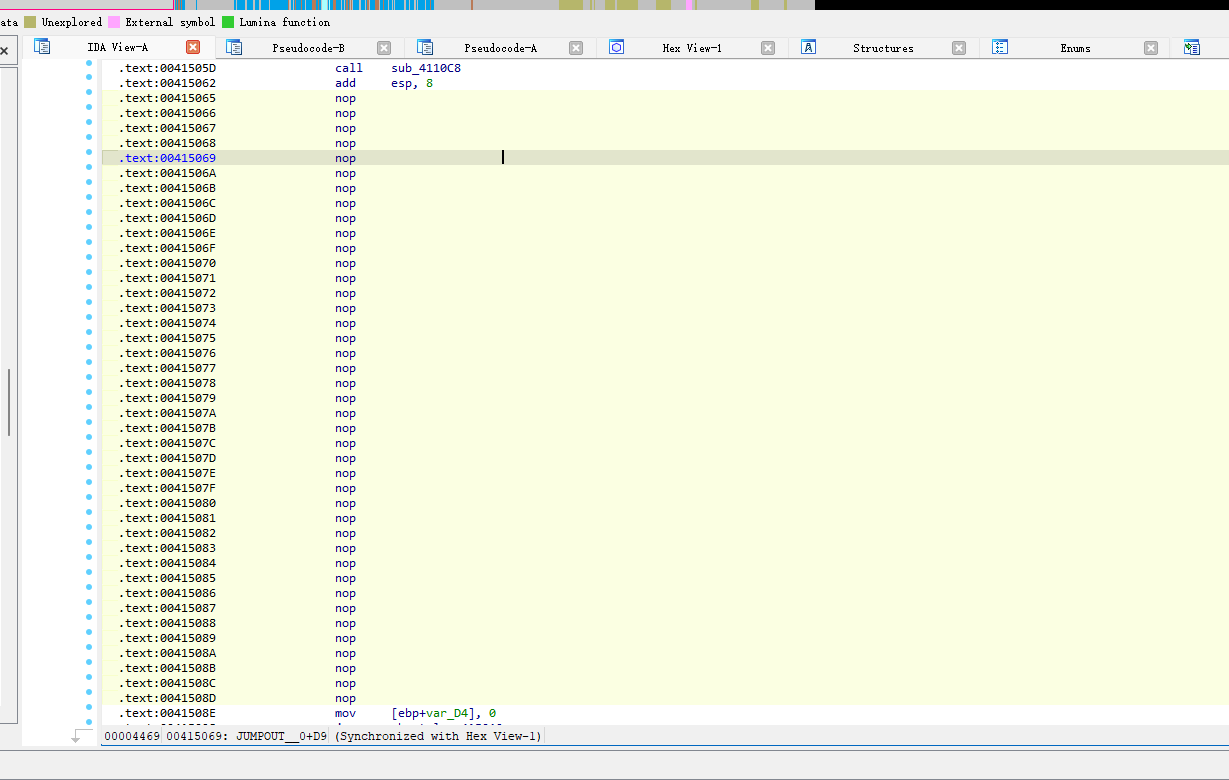
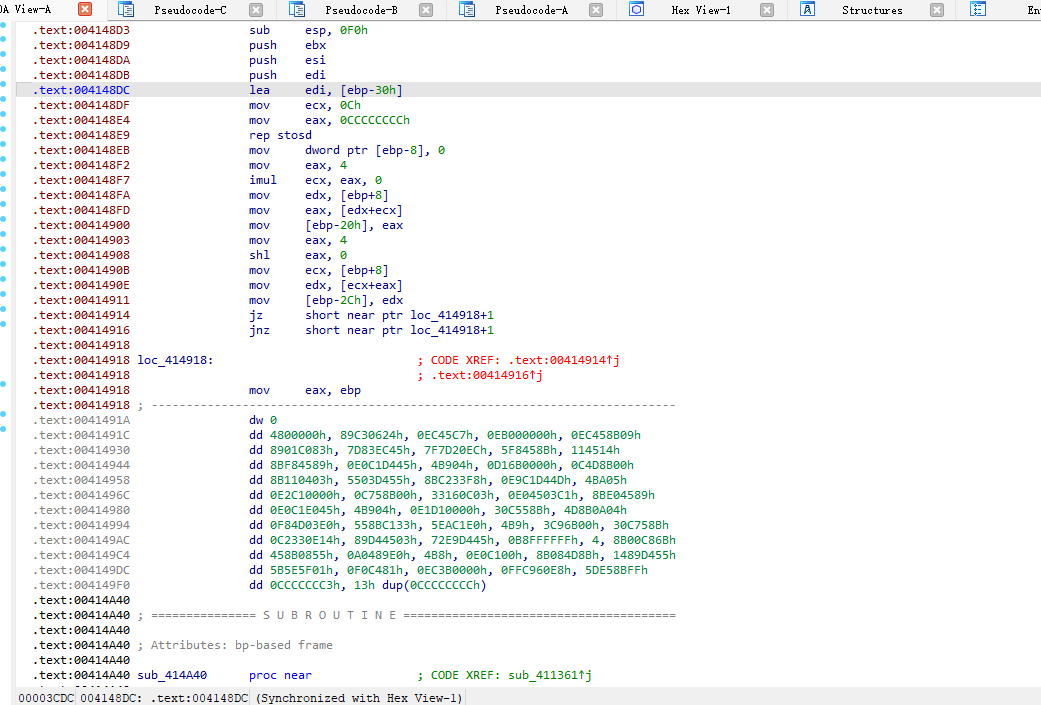
一些较为基础的花指令
全给抹了
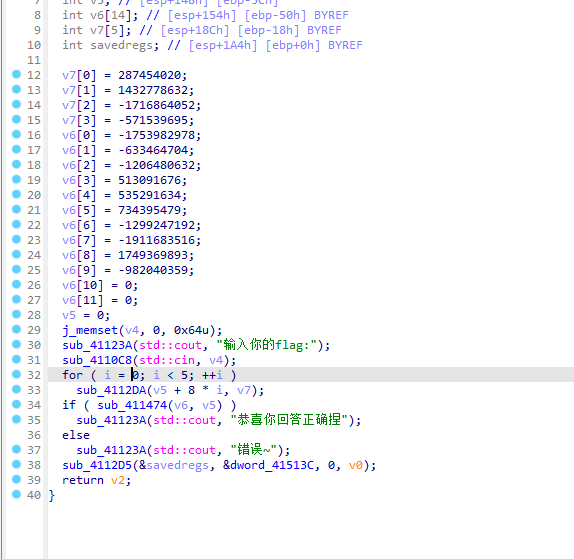
查看加密
抹除的大差不差
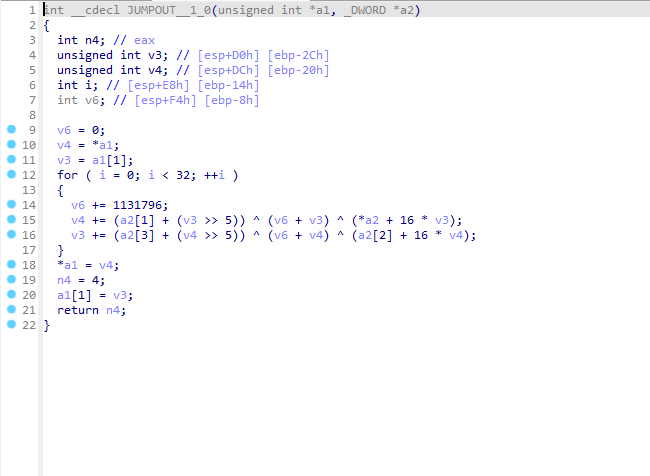
tea 脚本如下
1 | #include <stdio.h> |
pickle
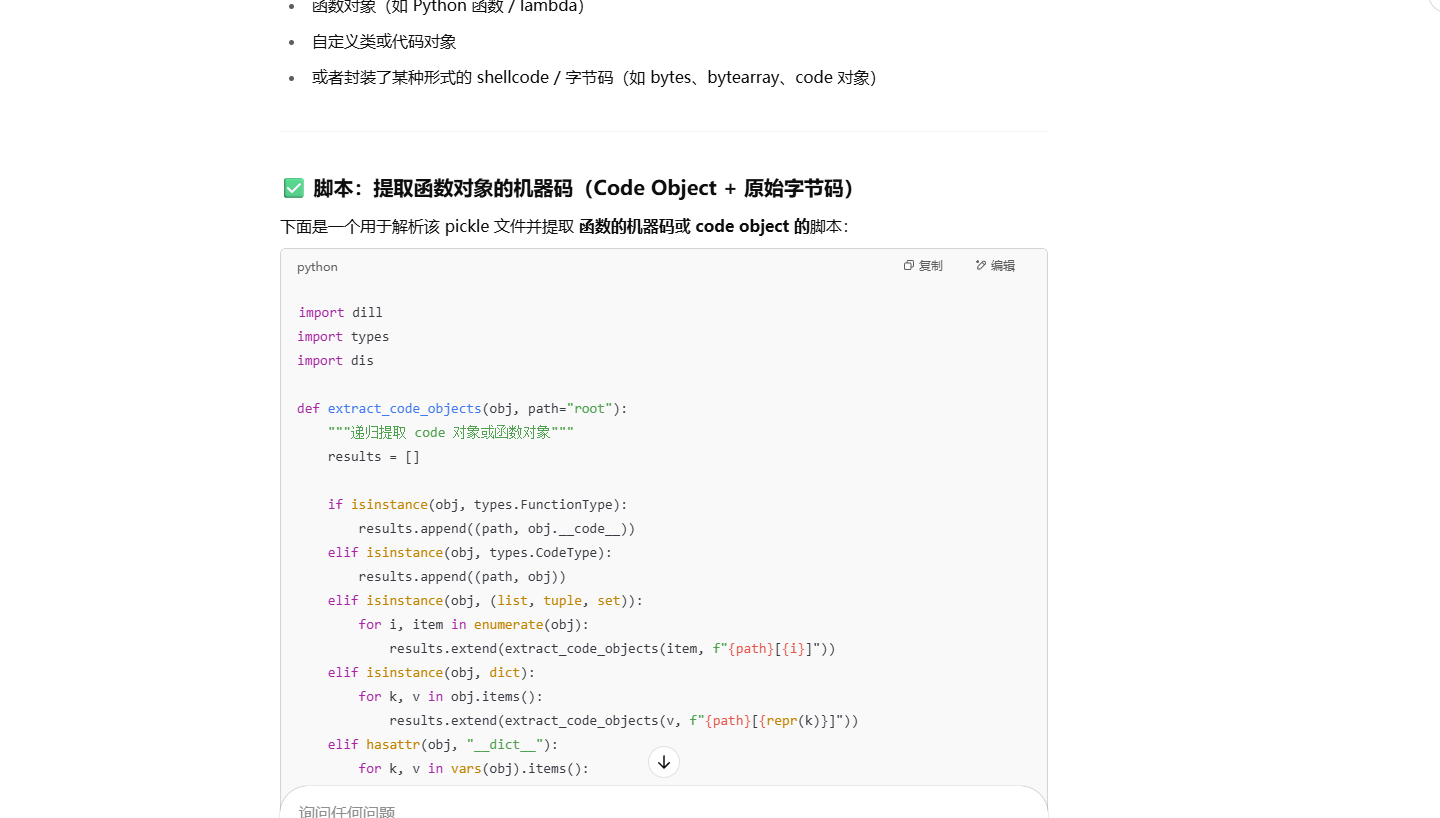
拷打ai获取脚本
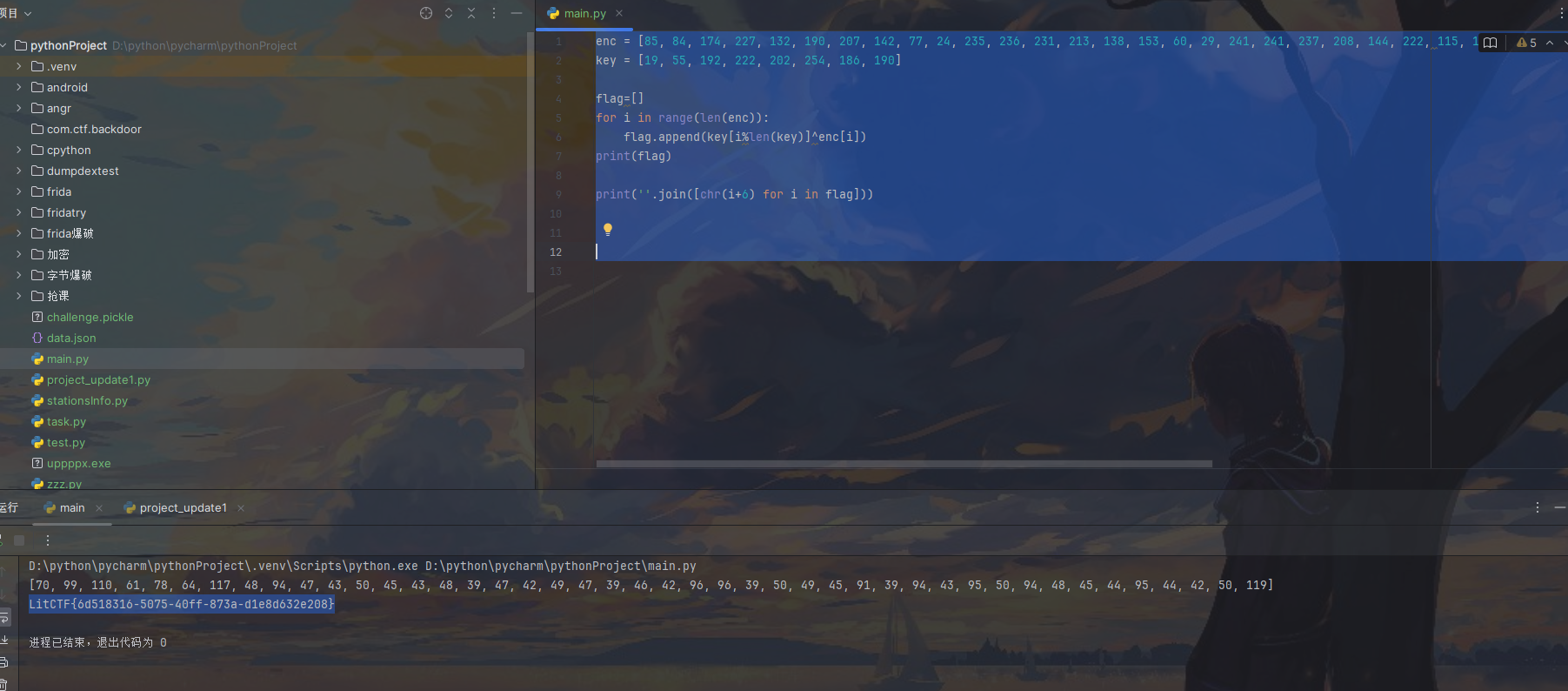
1 | import dill |
获取到字节码
1 |
|
继续拷打
1 | LitCTF{6d518316-5075-40ff-873a-d1e8d632e208} |
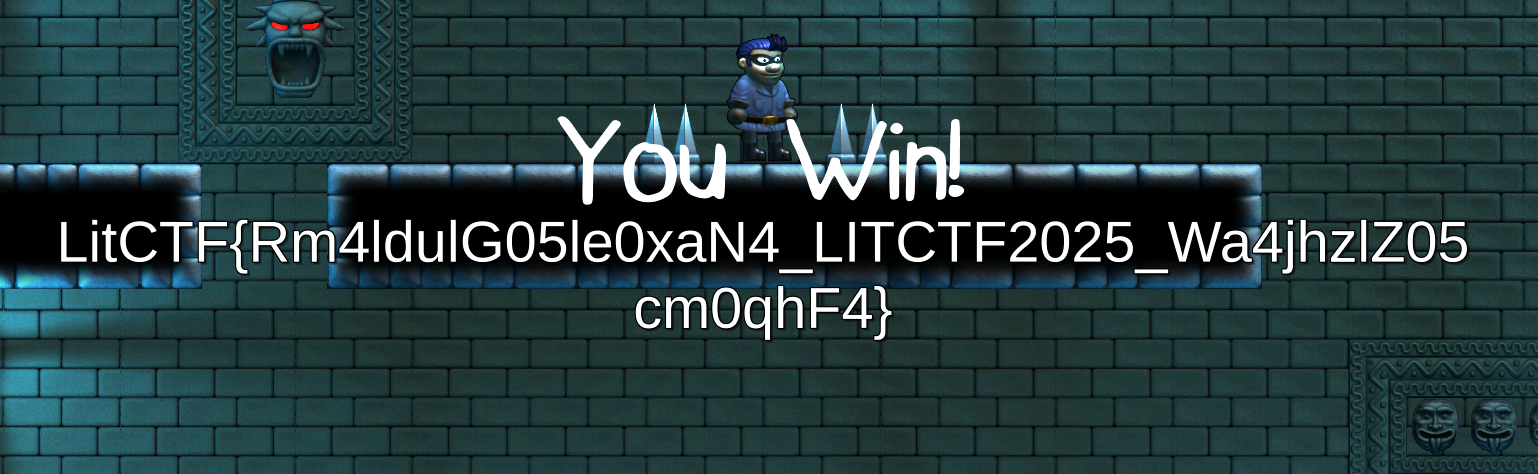
Robbie Wanna Revenge
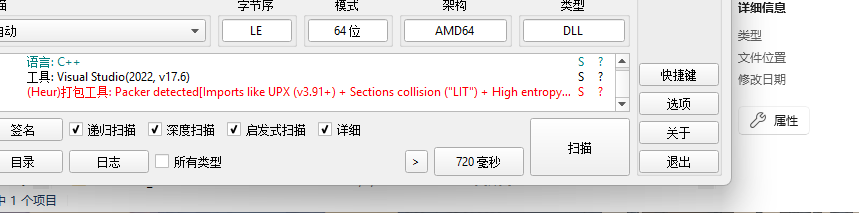
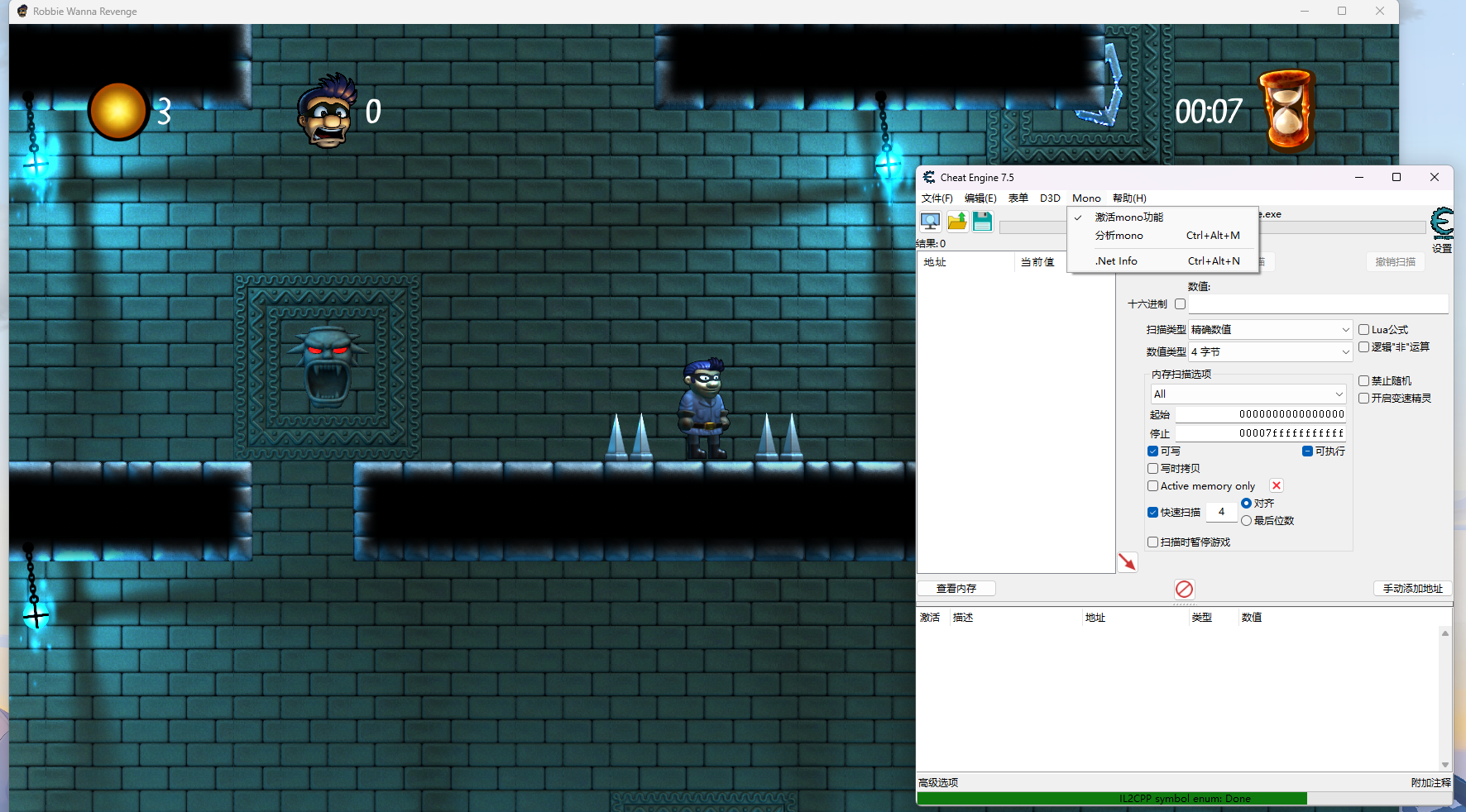
dll加壳 改了标志位即可完成
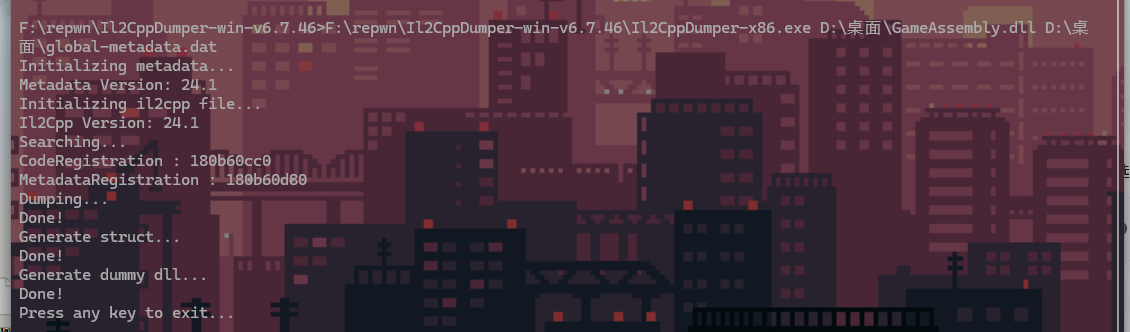
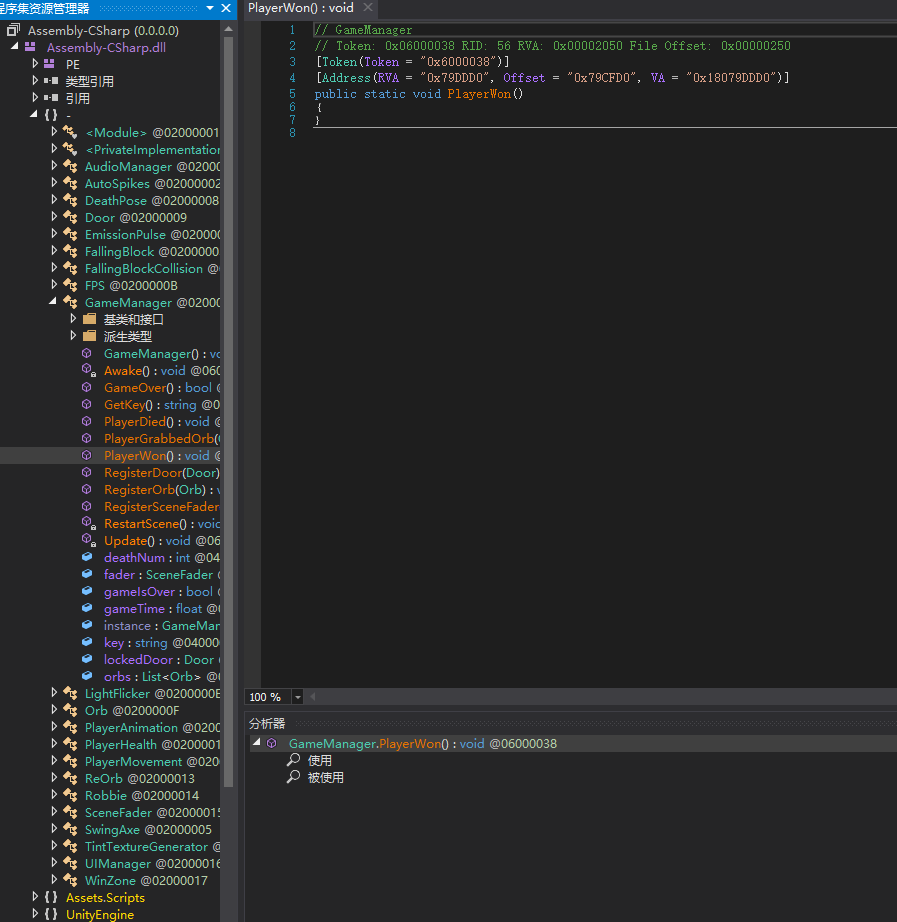
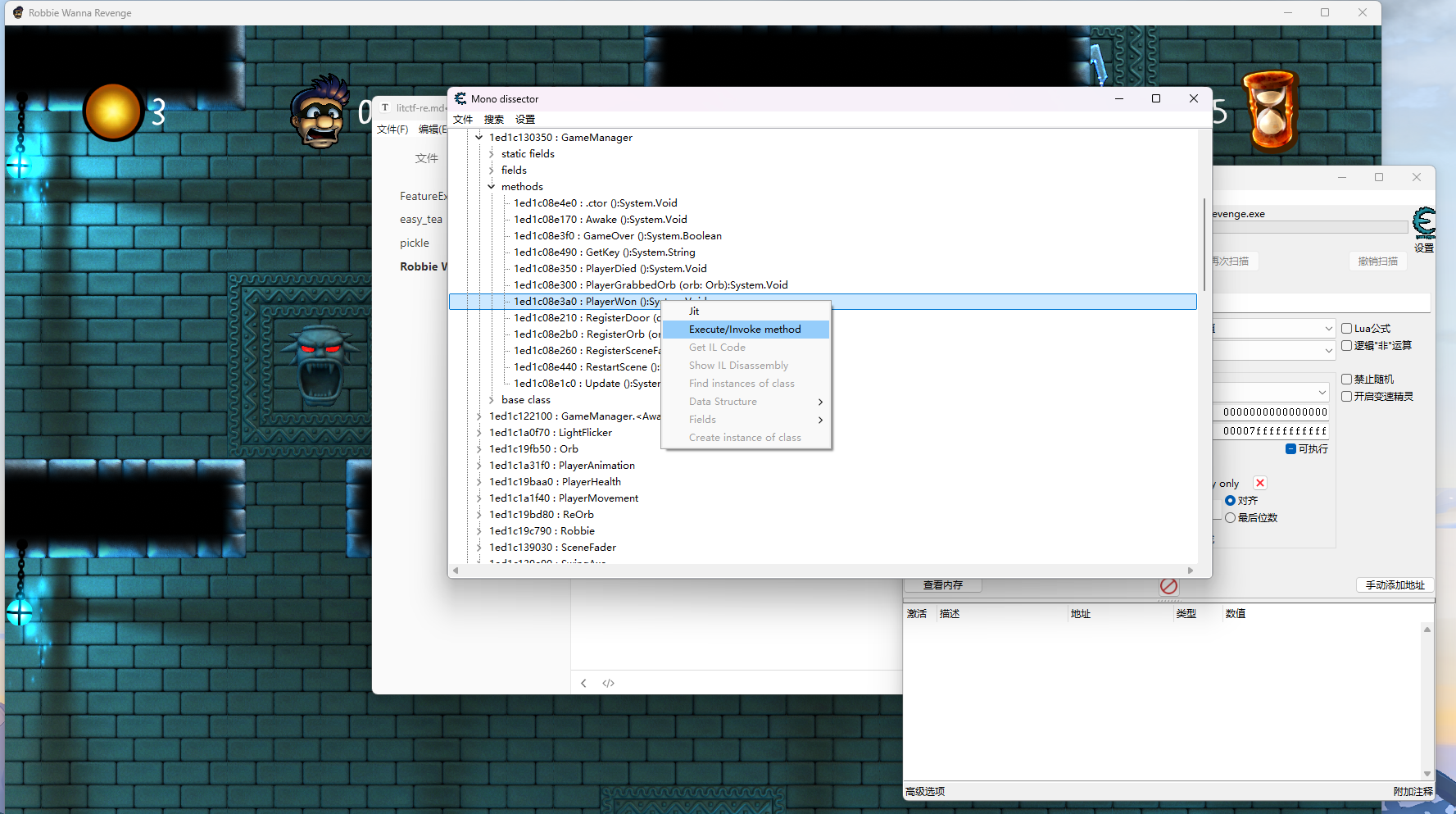
正常进行分析
我们可以看到有playerwon的东西