l3hctf-re-wp

l3hctf-re-wp
grandl3hctf
参考
Tauri 框架的静态资源提取方法探究 | yllhwa's blog
oacia/stalker_trace_so: 一个IDA插件,利用frida-stalker在加载so时打印出所有函数调用,解决frida-trace无法在so加载时trace的问题
frida-stalker-trace 使用并实战某音 | mgaic
ez_android
一开始想拿插件去trace的但是崩溃了 但是这个题不用trace也能做
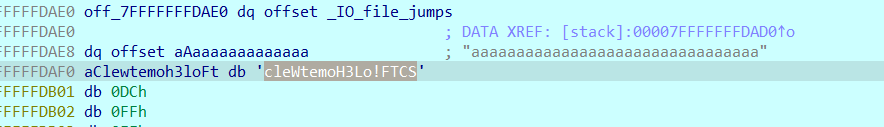
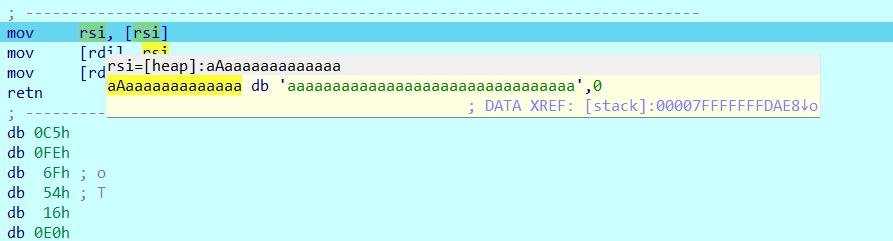
tauriactivity的app 解包静态资源
分别对应文件名及其长度 文件内容及其长度
1 | import os |
这里直接拿idapython更快点
1 | <!doctype html> |
解压的内容 就是js
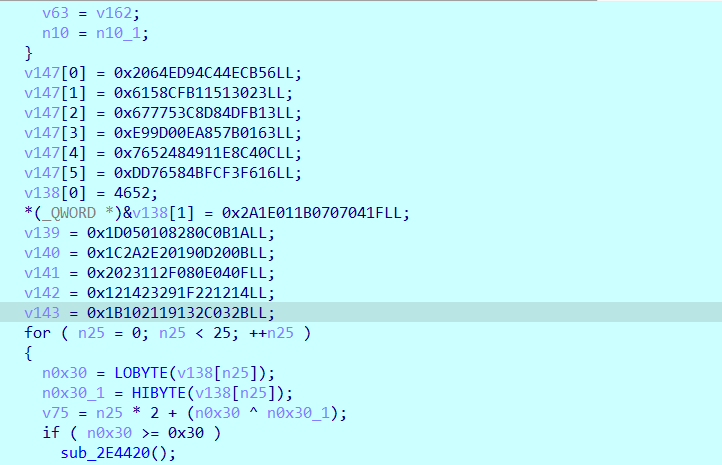
1 | {"$schema":"https://schema.tauri.app/config/2","productName":"ez_android","version":"0.1.0","identifier":"com.l3hctf.ezandroid","app":{"windows":[{"label":"main","create":true,"url":"index.html","dragDropEnabled":true,"center":false,"width":800.0,"height":600.0,"resizable":true,"maximizable":true,"minimizable":true,"closable":true,"title":"ez_android","fullscreen":false,"focus":true,"transparent":false,"maximized":false,"visible":true,"decorations":true,"alwaysOnBottom":false,"alwaysOnTop":false,"visibleOnAllWorkspaces":false,"contentProtected":false,"skipTaskbar":false,"titleBarStyle":"Visible","hiddenTitle":false,"acceptFirstMouse":false,"shadow":true,"incognito":false,"zoomHotkeysEnabled":false,"browserExtensionsEnabled":false,"useHttpsScheme":false,"javascriptDisabled":false,"allowLinkPreview":true,"disableInputAccessoryView":false}],"security":{"freezePrototype":false,"dangerousDisableAssetCspModification":false,"assetProtocol":{"scope":[],"enable":false},"pattern":{"use":"brownfield"},"capabilities":[]},"macOSPrivateApi":false,"withGlobalTauri":false,"enableGTKAppId":false},"build":{"devUrl":"http://localhost:1420/","frontendDist":"../dist","beforeDevCommand":"pnpm dev","beforeBuildCommand":"pnpm build","removeUnusedCommands":false},"bundle":{"active":true,"targets":"all","createUpdaterArtifacts":false,"icon":["icons/32x32.png","icons/128x128.png","icons/128x128@2x.png","icons/icon.icns","icons/icon.ico"],"useLocalToolsDir":false,"windows":{"digestAlgorithm":null,"certificateThumbprint":null,"timestampUrl":null,"tsp":false,"webviewInstallMode":{"type":"downloadBootstrapper","silent":true},"allowDowngrades":true,"wix":null,"nsis":null,"signCommand":null},"linux":{"appimage":{"bundleMediaFramework":false,"files":{}},"deb":{"files":{}},"rpm":{"release":"1","epoch":0,"files":{}}},"macOS":{"files":{},"minimumSystemVersion":"10.13","hardenedRuntime":true,"dmg":{"windowSize":{"width":660,"height":400},"appPosition":{"x":180,"y":170},"applicationFolderPosition":{"x":480,"y":170}}},"iOS":{"minimumSystemVersion":"13.0"},"android":{"minSdkVersion":24}},"plugins":{}} |
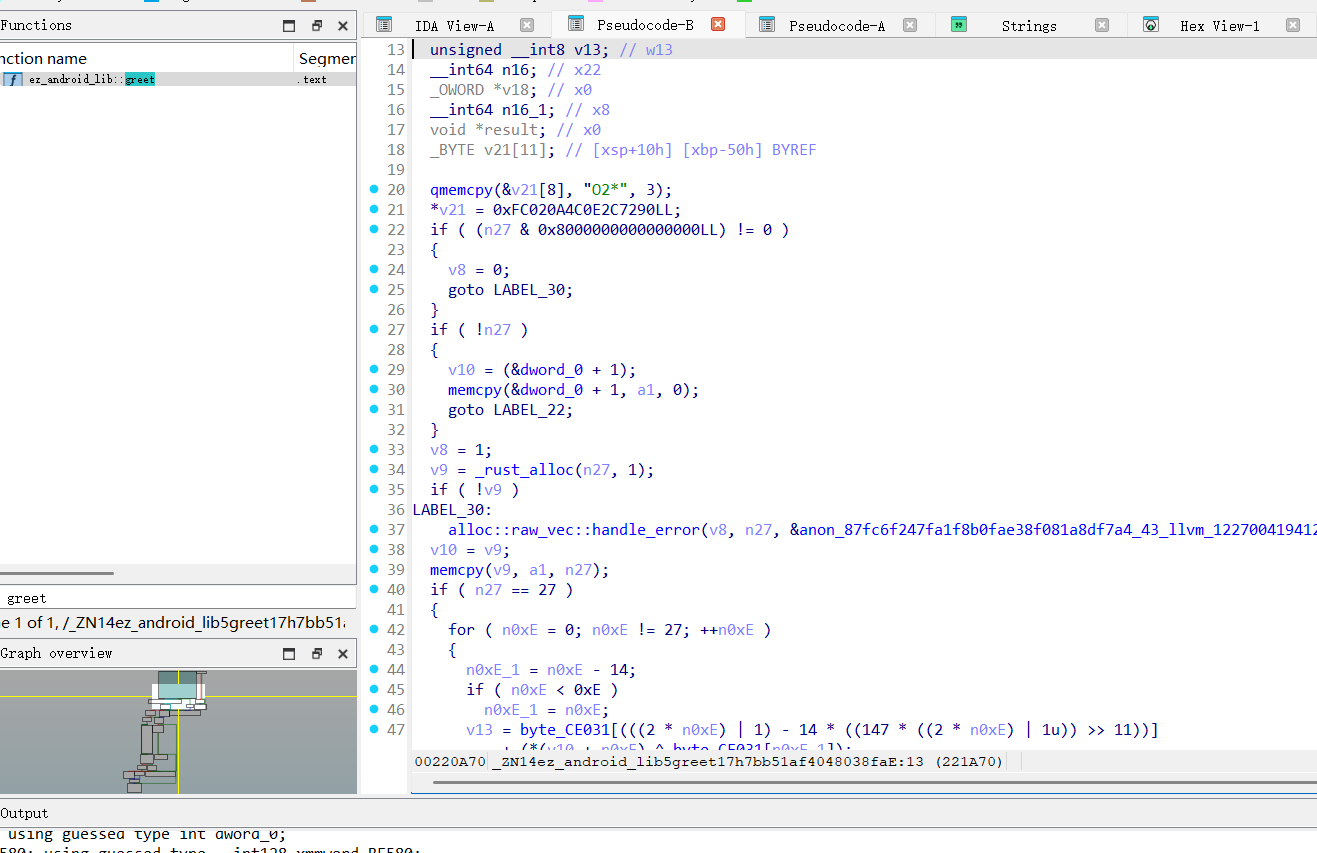
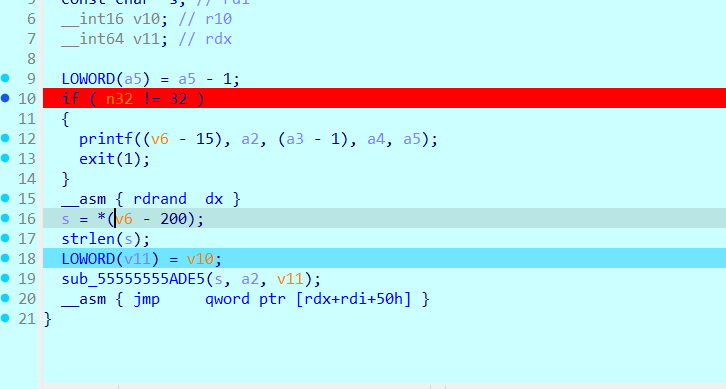
直接来到greet函数 单字节直接爆
1 | #include<stdio.h> |
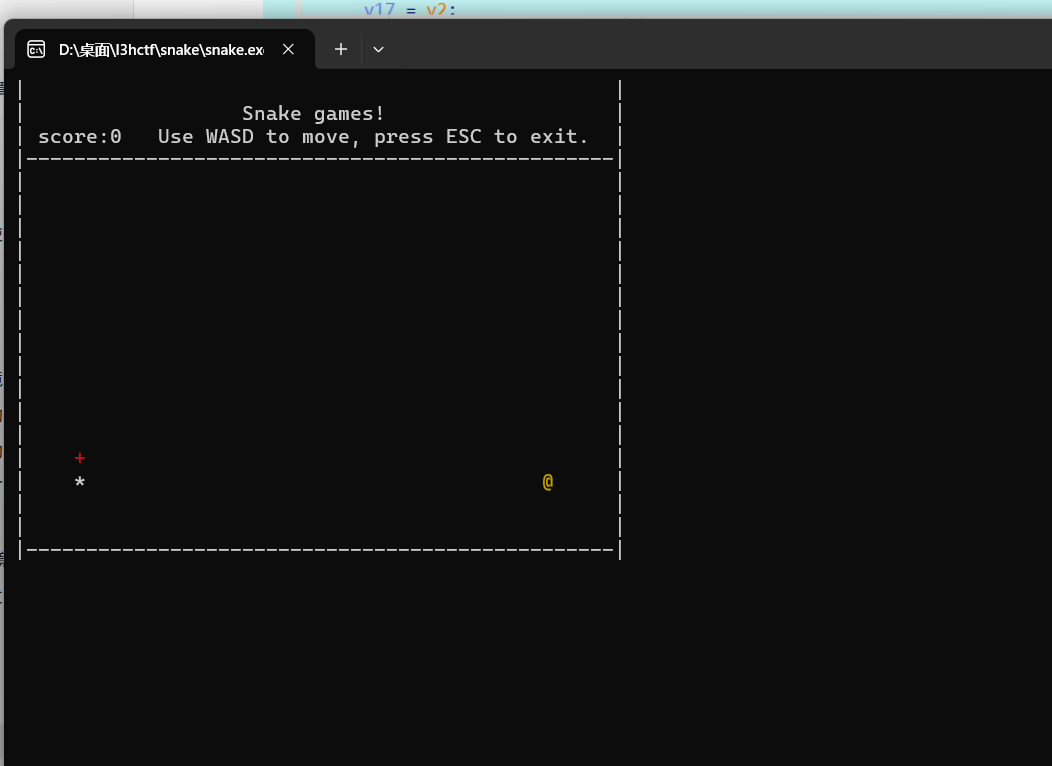
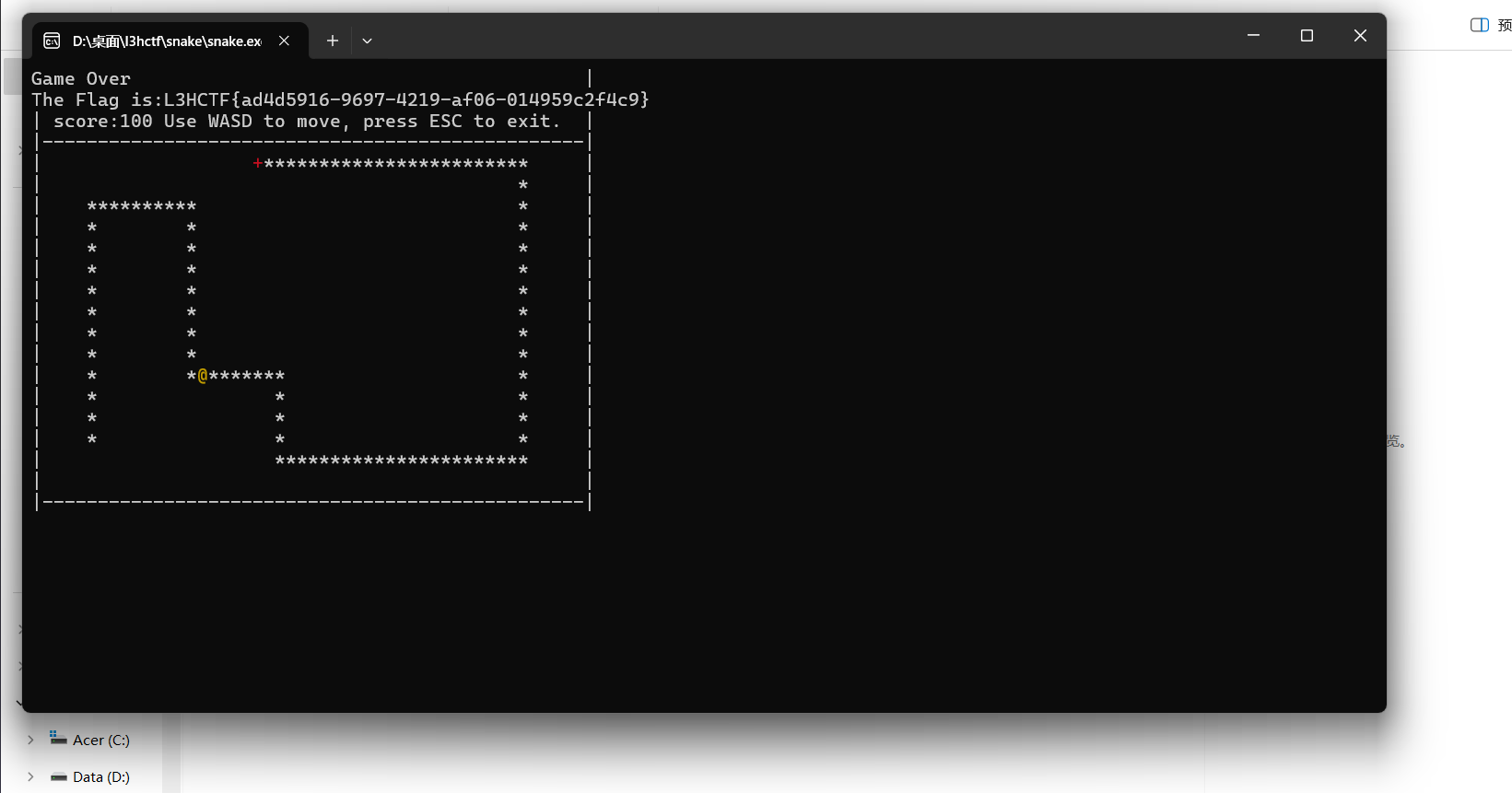
snake
遗憾败北 一开始就找到分数的地方 但是旁边就是rc4影响了判断 以为又是解密字符串 不然的话早出了 寄~~~~~~~~~~~~~~~~~~~~~~~
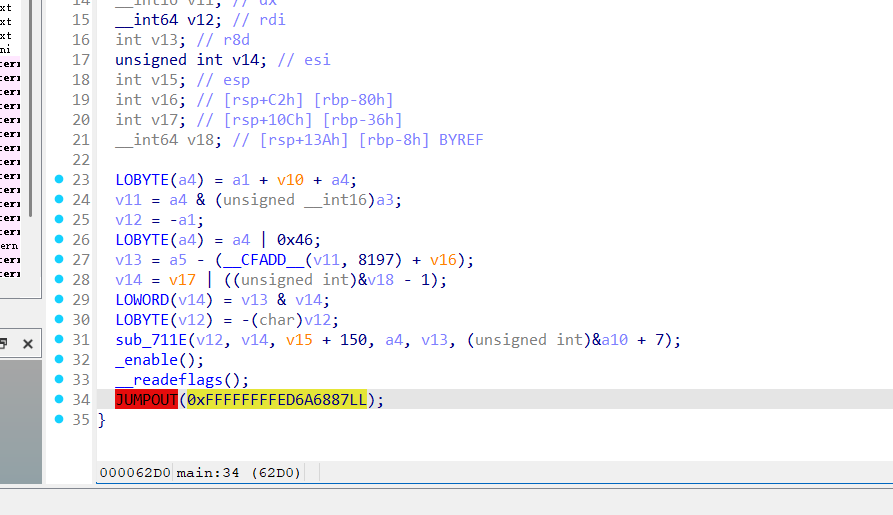
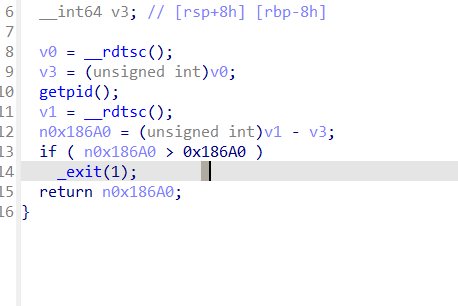
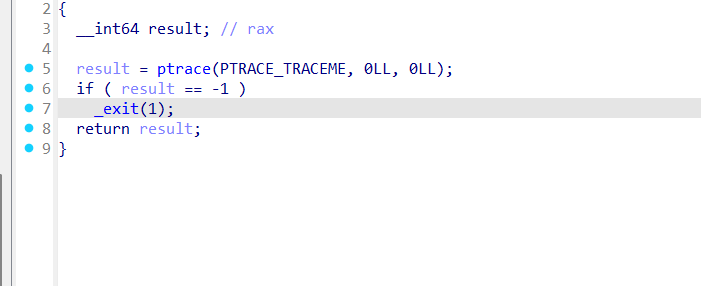
反调试我们使用
快速过掉 字符串查找可以看到一个base表 断读写断点
直接f9就到了使用base表解出 提示移动键的字符串 当然这里只是对程序的分析 接下来我们使用findcrypto去找 可以找到xxtea的内容 再去查看引用 断点
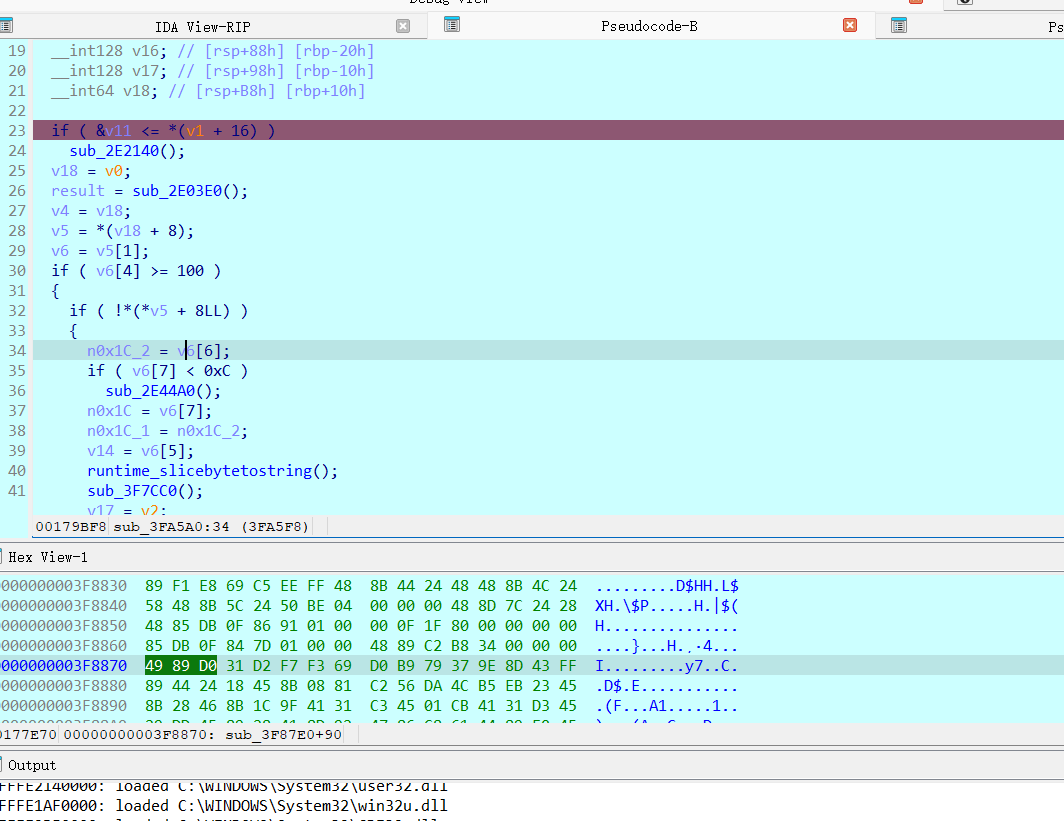
可以看到我们的内容是已经输出了 但是还没开始动 继续调试查找 判断逻辑
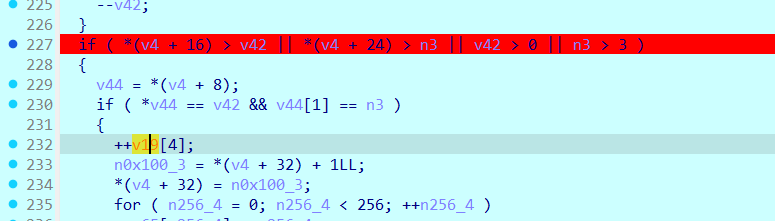
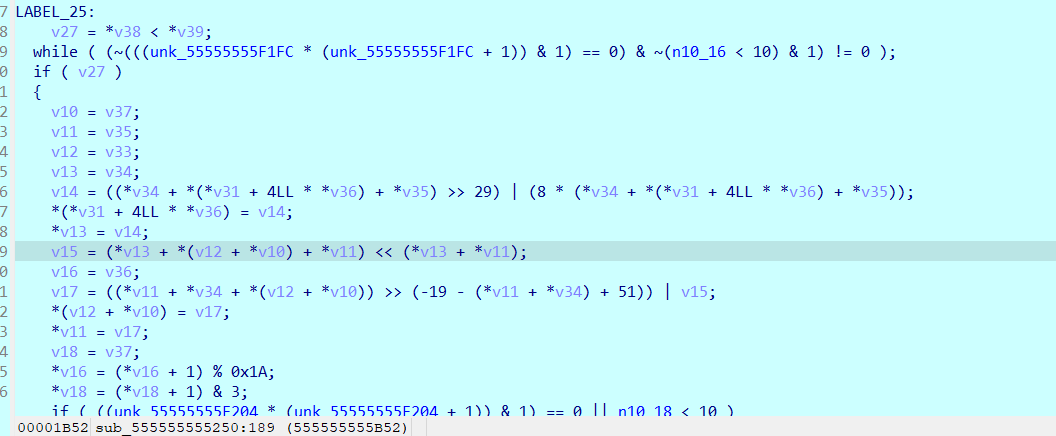
这里就是分数的地方 这里最好看汇编 c反编译的有点 这里就是判断全给他删除
obfuscate
小混淆问题不大
这些都不太影响执行走一遍就出来了 有几处反调试想要过一下 看看哪里跑飞了就进去断点慢慢调试 当然了你可以直接在scanf断点就完了
给我们的输入断个点好跟一下
到了这里
一路猛调就到了这里
其中有个地方赋值了
也就是key 继续分析
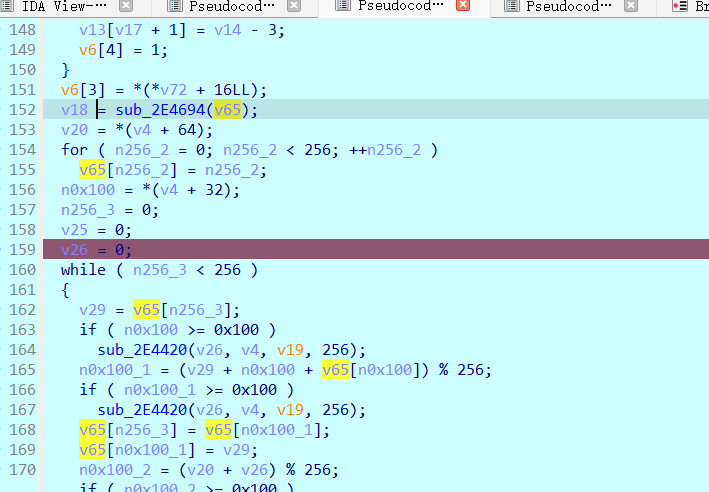
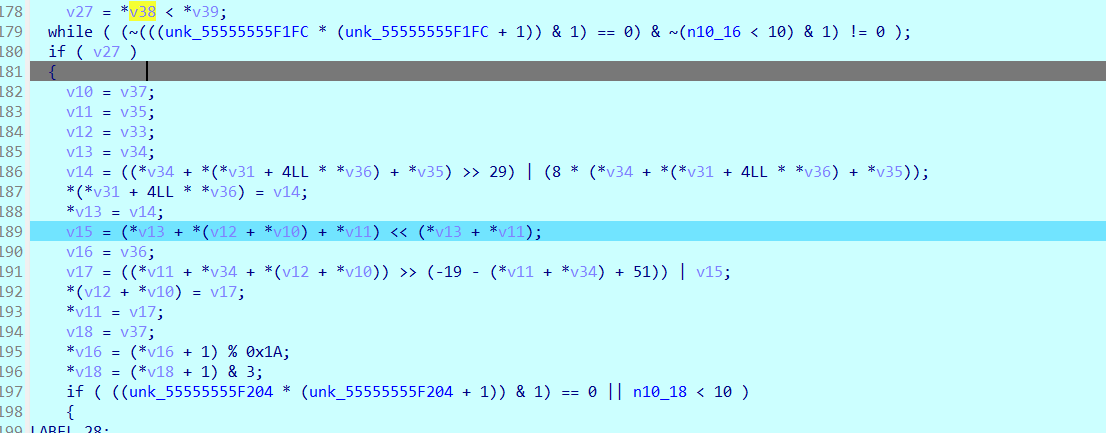
这一段就开始使用key生成一些东西
跑完那一段 可以看到key也被改了 断点继续跟踪
再次被引用
也就是这里
1 | __int64 __fastcall sub_555555555250(__int64 a1, __int64 a2) |
优化起来丢给ai 我反正是看不懂
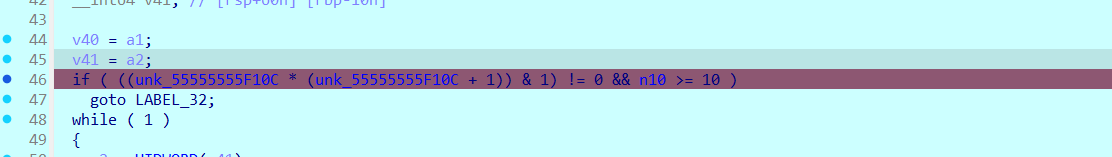
调试起来去看看使用key获取到的内容 由于我们在这里给了输入断点但是并没有发现这部分有关于输入的暂停 这里就是keybox的生成
断点在mov的寄存器 继续调试
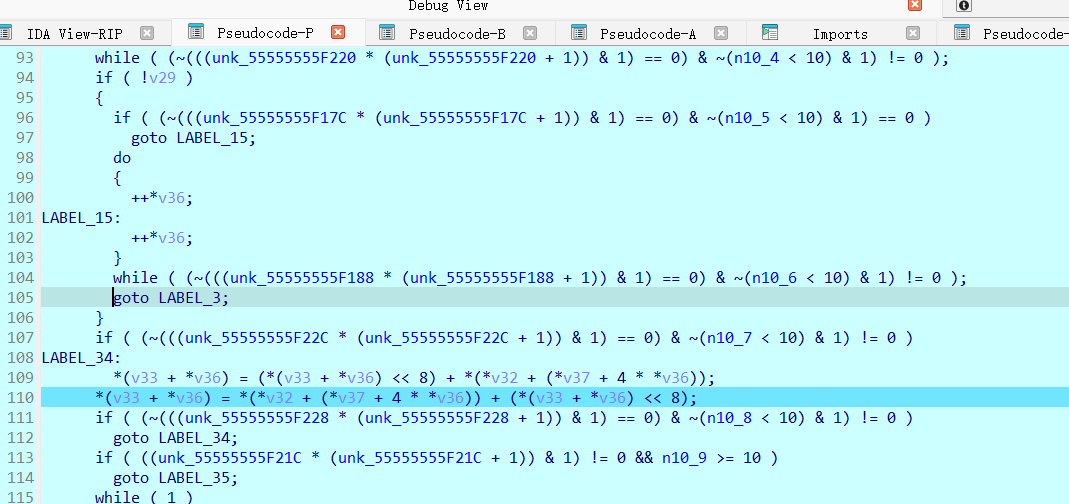
直接大跳就可以来到正确的加密位置 解一下混淆 分析一下流程 编写解密代码
1 | import struct |